Tor stands for The Onion Routing. Onion routing means that when you connect to the internet, all your internet traffic is routed through multiple servers and encrypted at each step. So, the uniqueness of the Tor browser is that it offers privacy, and its code is free and open-source.
In this age, when almost the whole world is connected online, there are also the problems of online tracking, censorship, and surveillance which can be real hurdles for those who do not want their identities to be revealed online or wish to have censor-free internet access. For them, the Tor browser can act as a savior. Using the Tor browser, one can connect to the internet anonymously. Even if someone tries to monitor the internet traffic of a Tor browser user, they will only be able to see that you are using Tor.
Installing the Tor browser
Go to https://www.torproject.org/download/ and click on the download option for the operating system on which you want to install Tor. You must use the official link to download Tor; otherwise, you might end up installing malware on your system in place of Tor.
After downloading the setup, the installation is like any other standard software installation. e.g., for Windows OS, just double-click on the setup file downloaded and confirm any prompt in the dialog box asking whether you want to install the software. Now, wait for it to finish installing.
The Tor browser is a portable software. So, once you have installed it, you can also run it from a USB drive. You need to select a location (a USB drive) to install during the setup.
First time run of Tor
There are some initial settings that you need to do when you run the Tor browser for the first time.
- You will see a network settings window when you open Tor for the first time. Here, you will see two options: connect and configure. The “connect” option should be clicked if your connection does not use any proxy or if your connection is not censored.
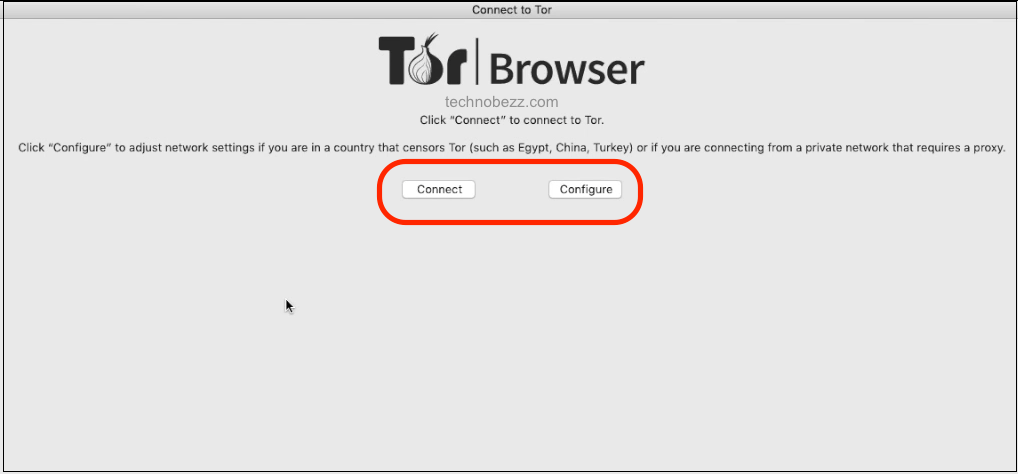
- After that, you will be connected to the Tor network after waiting for a while. The wait may be dependent on your internet connection.
- However, if your connection uses a proxy or is censored, you need to click on the “configure” option. Next, choose whether ‘Tor is censored in my country and/or use a proxy to connect to the internet’.
- Depending on your chosen option(s), you will be asked to choose some sub-options too.
- If you choose the ‘I used to connect to the internet” option, you will be asked to provide details of the proxy connection.
- If you chose the ‘Tor is censored in my country’ option, you need to choose how you want a bridge. That is, whether you want to ‘select a built-in bridge, request a bridge from torproject.org or provide a bridge I know’.
- Then click connect and wait for it to connect to the Tor network.
- After it is connected, you are done and can surf the internet anonymously.
Some facts and best practices
- The Tor browser is based on a modified version of the Firefox browser.
- Tor is available for Android, Windows, Mac OS X, and Linux operating systems.
- There is no backdoor in Tor. Also, the official Tor website promises that there will never be a backdoor in Tor.
- Additional plugins or add-ons installed in the Tor browser are not recommended as they may risk your privacy protection.
- You should use an HTTPS-encrypted connection for every website; otherwise, your internet traffic can be observed by the exit node in the Tor circuit.
- Tor browser is valid only for protecting your anonymity on the internet. Still, it cannot completely protect you from computer viruses or malware if you go to the darker parts of the web.
- You should avoid using torrents on the Tor network because it can reveal your IP address and thus can put your anonymity at risk.